What Is iptables and How to Use It for Network Security?
iptables is a command-line firewall utility that is used to manage the Linux kernel’s built-in firewall. It allows administrators to configure rules that control how packets are handled by the kernel’s networking stack. These rules can be used to allow or block incoming or outgoing traffic based on various criteria, such as source and destination IP addresses, ports, and protocols.
The iptables firewall operates by defining a set of chains, which are groups of rules that are applied to incoming or outgoing network packets. The most commonly used chains are the INPUT chain, which is applied to incoming packets, the OUTPUT chain, which is applied to locally-generated packets, and the FORWARD chain, which is applied to packets that are being forwarded through the machine.
Each chain is made up of a series of rules, which specify what action should be taken for packets that match certain criteria. The rules are processed in order, and the first rule that matches a packet is the rule that is applied. iptables supports many different matching criteria, such as IP addresses, ports, and packet headers, as well as various actions, such as dropping or accepting packets, and logging or redirecting packets to other chains.
Iptables is powerful tool that is widely used to configure the firewall on Linux systems, It’s important to note that it is not the only firewall solution on Linux, another alternative is nftables which is replacement of iptables and provides a more powerful and flexible firewall solution than iptables.
Why use iptables?
There are several reasons why you might use iptables to configure a firewall on a Linux system:
- Security: One of the primary reasons to use iptables is to improve the security of a system by controlling which network traffic is allowed to reach it. With iptables, you can set rules to block incoming traffic from known malicious sources, and only allow traffic from trusted sources.
- Access Control: Iptables can also be used to control access to services running on a system. For example, you can use iptables to only allow incoming connections to a web server from specific IP addresses or subnets, or to block incoming connections to a service on a specific port.
- Traffic Management: Iptables can be used to manage the flow of network traffic on a system. You can use iptables to prioritize certain types of traffic, such as real-time applications, or to limit the amount of bandwidth that a specific IP address or service can use.
- NAT: Iptables is capable of performing NAT (Network Address Translation) which enables devices on a local network to access the Internet through a single public IP address. It can also be used to forward specific ports to internal servers on a network, allowing them to be accessed remotely.
- Provide a base for other tools: Iptables can be integrated with other tools such as fail2ban and ufw, which can be used to simplify the management of firewall rules.
- Advanced use-cases: iptables offers much more flexibility and granularity in terms of filtering packets, providing advanced use cases that other firewalls may not provide.
It is worth noting that while iptables is a powerful and flexible tool, it can be complex to set up and manage, especially for large or complex networks. It is important to have a good understanding of network security and Linux administration before configuring a firewall with iptables.
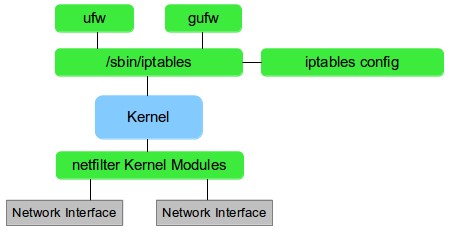
How to Use iptables?
- Viewing the current firewall rules: To view the current firewall rules, you can use the iptables command without any options or arguments. This will display the current rules in all of the default chains (INPUT, FORWARD, and OUTPUT).
- Adding a new rule: To add a new rule to the firewall, you can use the iptables command with the -A option, which stands for “append.” For example, to allow incoming SSH traffic, you can use the following command:
iptables -A INPUT -p tcp --dport 22 -j ACCEPTThe above command will append a rule to the INPUT chain that allows incoming traffic to TCP port 22 (the default SSH port) and will match packets that are “jumped” to the ACCEPT target
- Deleting a rule: To delete a rule, you can use the iptables command with the -D option, which stands for “delete.” For example, to delete a rule that allows incoming SSH traffic, you can use the following command:
iptables -D INPUT -p tcp --dport 22 -j ACCEPTThis will delete a rule from the INPUT chain that allows incoming traffic to TCP port 22 and jumps packets to the ACCEPT target
- Saving firewall rules: To save the current firewall rules so that they will persist after a reboot, you can use the iptables-save command to save the current rules to a file, and then use the iptables-restore command to restore the saved rules on reboot.
iptables-save > /etc/iptables.rules
This will save the current firewall rules to /etc/iptables.rules file, and it could be automatically restored by systemd on startup.
- Clearing all the firewall rules: If you want to clear all the rules that are currently set in the firewall, you can use the iptables command with the -F option, which stands for “flush.”
iptables -F
This command will flush all the chains, so all the rules in all chains are deleted
It’s important to note that the commands above are basic examples and that iptables can be customized to suit more complex needs and scenarios, such as configuring a firewall for a server, blocking specific IP addresses, and creating custom chains.